Blog


Certificate management is an important process that is a part of an organization’s security program. Certificate management handles the acquisition and deployment, tracking renewals, usage and expiration of SSL certificates. SSL certificates are used to encrypt traffic between websites and users to ensure the data transmitted is protected against disclosure and modification. SSL/TLS is an encrypted tunnel that enables the secure exchange of sensitive information.
Certificate management is required to ensure data is adequately protected; without certificate management, data transmitted between websites and users may be at risk. A specific type of certificate, a wildcard certificate, is occasionally used as they have the added benefit of being more efficient to replace and cost-effective to renew. However, there are security risks associated with these types of certificates, and many of the benefits have become trivial.
What is a wildcard certificate?
A wildcard certificate is a certificate that can be used for multiple sub-domains of a domain. For example, a wildcard certificate for google could be issued for “*.google.com” and used on the sites “mail.google.com”, “contact.google.com”, “video.google.com”, or any other sub-domain. When you visit a website, such as google.com and see the secured green lock next to the address bar, that is due to proper implementation of a valid SSL/TLS certificate.
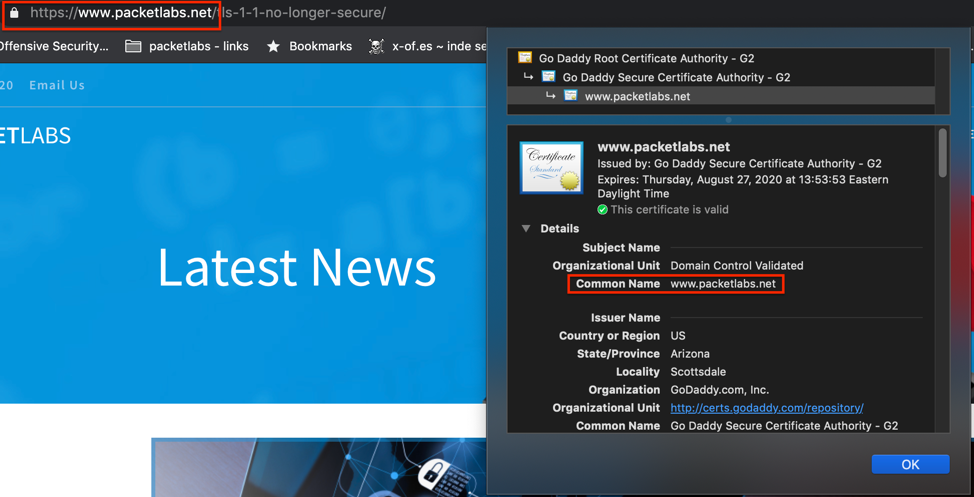
Users can trust the website is who it claims to be, and all traffic between the user and website is protected with secure encryption. When you visit a website, your browser compares the Common Name of the certificate and compares it against the sites address, if they match the site’s identity is valid. In the below example our website, www.packetlabs.net as seen in the address bar matches the common name on the issued certificate.
Why Use Wildcard Certificates?
Using wildcard certificates allows organizations to use a single certificate for all subdomains. There are multiple reasons why wildcard certificates may be used; the most commonly encountered reasons are:
Easier to renew a single certificate
Cheaper to purchase one certificate for many sites, than a certificate for each site
Easier to manage; one certificate, one expiration date.
Additionally, some platforms, such as web development or cloud hosting may be designed to use wildcard certificates when subdomains are programmatically generated. Using wildcards should be done with caution, and only when all the risks are understood and there are no other options.
Security Risks of Wildcard Certificates
When a wildcard certificate is reused across multiple subdomains hosted on multiple servers, there are additional security concerns for the protections offered by SSL/TLS certificates. In the event of a breach of one of the servers, the certificate will be compromised by adversaries. The confidentiality and integrity of traffic to each site where the certificate is used is jeopardized. An attacker who obtains the certificate would be able to decrypt, read or modify, and re-encrypt traffic. This is likely to result in the disclosure of sensitive information and further targeted attacks.
In the event of a server breach, to limit the damage, each server should have a unique certificate that is valid only for the subdomains and sites it is hosting should. With services such as Let’s Encrypt offering free certificates and multiple solutions for automated certificate renewal and deployment, there is almost no need to use wildcard certificates. Further, wildcard certificates lend themselves to mishandling of private keys. If not stored or transferred securely, they may be compromised requiring a certificate revocation.
Packetlabs specializes in Penetration testing of web and mobile applications, networks and infrastructure, vulnerability management, and red team engagements. For more information on how Packetlabs can improve your web application security, please do not hesitate to contact us.