CYRISMA Sensor Version 2.5 for Windows: A Technical Deep-Dive
Would you like to learn more?
Download our Pentest Sourcing Guide to learn everything you need to know to successfully plan, scope, and execute your penetration testing projects.
Authored by Packetlabs ethical hackers Eric Salario and Chance Pearson.
During our Assumed Breached Penetration Testing (ABPT) engagements, we are typically provided access to a user workstation. The client decides which identity will be mimicked, but usually it will be a user without local administrator access to their own workstations. As a result, identifying local privilege escalation paths sometimes becomes necessary.
While escalating privileges on the assumed-breached system isn’t always required, we found it to be highly needed in one of our engagements as part of an attack path. This is where we discovered a couple of privilege escalation opportunities:
Insecure folder permissions leading to a service binary hijacking
DLL hijacking
These techniques are hardly groundbreaking. In fact, it’s one of the oldest tricks in the Windows privilege escalation playbook. Yet, during a recent engagement, we encountered these issues in an application we didn’t expect: a cyber risk management product designed to improve security posture.
Insecure Folder and File Permissions (CVE-2025-57624)
CYRISMA Sensor Version 2.5 for Windows has an Insecure Folder and File Permissions vulnerability. A low-privileged user can abuse these issues to escalate privileges and execute arbitrary code in the context of NT AUTHORITY\SYSTEM by replacing DataSpotliteAgent.exe or any other binaries called by the Cyrisma_Agent service when it starts.
To reproduce this issue, download and install Cyrisma_Setup.exe (this needs a demo or a valid license from the vendor).
Installation Behavior
During installation of the CYRISMA Agent, it performs checks then uses a provided agent key and instance URL to validate licensing and initiate pairing with the CYRISMA cloud.
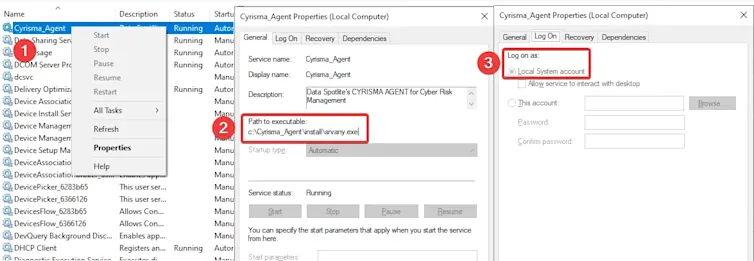
Interestingly, the agent is then installed as a Windows service Cyrisma_Agent with binary pointing to srvany.exe, and file permissions are modified to remove access rights for the BUILTIN\Users and Authenticated Users groups from this service binary, but not for the rest of the stuff within the directory.
[04/25/25 09:15:52] - ----- CYRISMA Agent Installation Started---- [04/25/25 09:15:52] - Attempting to force tls 1.2... [04/25/25 09:15:52] - SYSTEM INFORMATION: [04/25/25 09:15:52] - ------------------- [04/25/25 09:15:52] - Operating Sytem: Microsoft Windows 10 Pro [04/25/25 09:15:52] - Machine Name: PKT-WKS01 [04/25/25 09:15:52] - Local Ethernet IP Addrese(es): [04/25/25 09:15:54] - [04/25/25 09:15:54] - Local Wi-Fi IP Address(es): [04/25/25 09:15:54] - [04/25/25 09:15:54] - Local Time Zone: (UTC-08:00) Pacific Time (US & Canada) [04/25/25 09:15:54] - Verifying connectivity to msp.cyrisma.com... [04/25/25 09:15:54] - Verified. Public Facing IP: [REDACTED] [04/25/25 09:15:54] - Attempting to get local machine identifier... [04/25/25 09:15:54] - [REDACTED] [04/25/25 09:15:54] - ------------------- [04/25/25 09:15:54] - Switches: Key: [REDACTED] url: https://[REDACTED].cyrisma.com mode: agent autoprovision: yes [04/25/25 09:15:54] - Checking if key: [REDACTED] is valid with instance: https://[REDACTED].cyrisma.com [04/25/25 09:15:54] - Instance URL is: https://[REDACTED].cyrisma.com [04/25/25 09:15:54] - Validating licensing and pairing agent with: https://[REDACTED].cyrisma.com/app/installer/events/323032[REDACTED]3544?autoprovision=yes [04/25/25 09:15:55] - Key Validation Success. Checking for Dot Net... [04/25/25 09:15:55] - Validating Dot Net install: [04/25/25 09:15:56] - Cyrisma Install Checker ----------------------- Checking for .NET... .NET Framework (short version) = 4.8 .NET Framework (entire version) = .NET Framework 4.8.4614.0 .NET MS Release (from registry) = 528372 .NET MS Version = 42000 Result = Installed
[04/25/25 09:15:56] - Installing Agent Service... [04/25/25 09:15:58] - Setting rights for srvany.exe... [04/25/25 09:15:58] - Removing rights for BUILTIN Users: [04/25/25 09:15:58] - processed file: c:\Cyrisma_Agent\install\srvany.exe Successfully processed 1 files; Failed processing 0 files [04/25/25 09:15:58] - Removing rights for Authenticated Users: [04/25/25 09:15:58] - processed file: c:\Cyrisma_Agent\install\srvany.exe Successfully processed 1 files; Failed processing 0 files [04/25/25 09:15:58] - CYRISMA Agent Setup Complete... |
Abusing The Issue
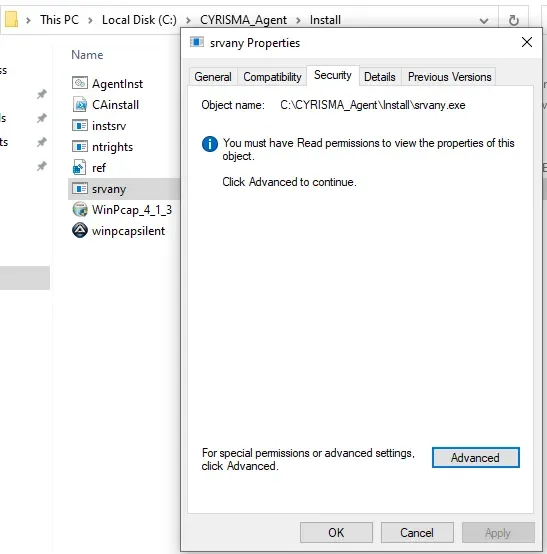
When the permissions on all files and folders inside C:\CYRISMA_Agent is reviewed, Authenticated Users were observed to have Modify, Read & Execute, List Folder Contents, Read, and Write permissions on the folder and its contents, except for srvany.exe located at C:\CYRISMA_Agent\Install, where access for BUILTIN\Users and Authenticated Users has been explicitly removed during installation.
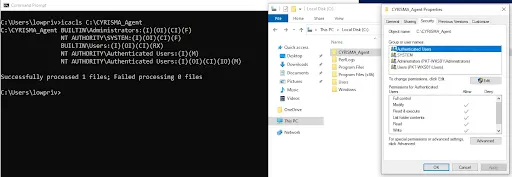
A Windows service Cyrisma_Agent that runs as Local System (NT AUTHORITY\SYSTEM) is created upon installation. This runs the service binary C:\CYRISMA_Agent\Install\srvany.exe. Low privilege users don’t have access to this service and to the service binary.
Using a tool like Sysinternals' Procmon, it was observed that srvany.exe spawns DataSpotliteAgent.exe when the Cyrisma_Agent service starts.
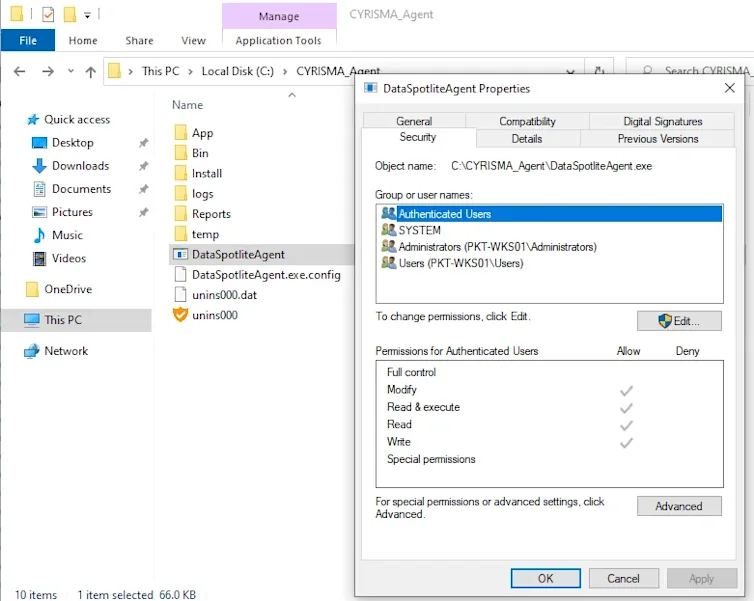
This behavior can be abused by replacing DataSpotliteAgent.exe with an arbitrary binary of your choosing. Upon service restart, the binary will be executed with SYSTEM privileges.
Watch the full demo video today.
DLL Hijacking (CVE-2025-57625)
DLL hijacking vulnerability in CYRISMA Agent version 2.5 allows local users to escalate privileges and execute arbitrary code via multiple DLLs.
Abusing the Issue
Using Sysinternals' Procmon, DLLs that DataSpotliteAgent.exe was loading during runtime at the same directory, which doesn't exist, were enumerated.
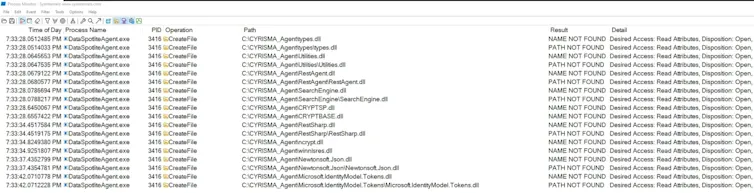
In this case, we chose to hijack one of the DLLs CRYPTBASE.dll.
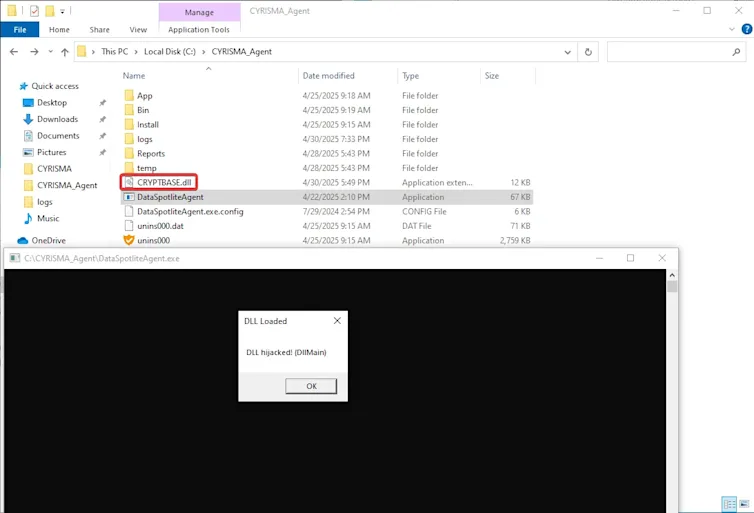
Note that the issue exists regardless of the directory. For instance, the DataSpotliteAgent.exe was moved to the Desktop, and it's calling the DLLs in its current directory.
Learn more via our demo video.
Disclosure Timeline
2025-04-23: Discovery
2024-04-24: Initial vendor notification
2024-05-01: Initial vendor response
2025-05-13: Release of fixed version/patch
2025-07-07: Public disclosure
Conclusion
Even mature security products can introduce basic Windows privilege-escalation risks when installation paths, file permissions, or DLL loading aren’t hardened. Our engagement shows that simple checks such as folder ACLs and safe DLL search paths catch high-impact issues before attackers do.
Thanks to CYRISMA for acknowledging and fixing the vulnerability quickly! The fixed version (CYRISMA Sensor Version 444) has been pushed to their customers.
Contact Us
Speak with an Account Executive
Interested in Pentesting?

Penetration Testing Methodology
Our Penetration Security Testing methodology is derived from the SANS Pentest Methodology, the MITRE ATT&CK framework, and the NIST SP800-115 to uncover security gaps.
Download Methodology
Pentest Sourcing Guide
Download our Pentest Sourcing Guide to learn everything you need to know to successfully plan, scope, and execute your penetration testing projects.
Download GuideExplore in-depth resources from our ethical hackers to assist you and your team’s cyber-related decisions.

September 13 - Blog
Why Multi-Factor Authentication is Not Enough
Knowing is half the battle, and the use and abuse of common frameworks shed insight into what defenders need to do to build defense in depth.

November 19 - Blog
The Top Cybersecurity Statistics for 2024
The top cybersecurity statistics for 2024 can help inform your organization's security strategies for 2025 and beyond. Learn more today.

October 24 - Blog
Packetlabs at SecTor 2024
Packetlabs is thrilled to have been a part of SecTor 2024. Learn more about our top takeaway's from this year's Black Hat event.







